Abstract
We construct the currently most efficient signature schemes with tight multi-user security against adaptive corruptions. It is the first generic construction of such schemes, based on lossy identification schemes (Abdalla et al.; JoC 2016), and the first to achieve strong existential unforgeability. It also has significantly more compact signatures than the previously most efficient construction by Gjøsteen and Jager (CRYPTO 2018). When instantiated based on the decisional Diffie–Hellman assumption, a signature consists of only three exponents.
We propose a new variant of the generic construction of signatures from sequential OR-proofs by Abe, Ohkubo, and Suzuki (ASIACRYPT 2002) and Fischlin, Harasser, and Janson (EUROCRYPT 2020). In comparison to Fischlin et al., who focus on constructing signatures in the non-programmable random oracle model (NPROM), we aim to achieve tight security against adaptive corruptions, maximize efficiency, and to directly achieve strong existential unforgeability (also in the NPROM). This yields a slightly different construction and we use slightly different and additional properties of the lossy identification scheme.
Signatures with tight multi-user security against adaptive corruptions are a commonly-used standard building block for tightly-secure authenticated key exchange protocols. We also show how our construction improves the efficiency of all existing tightly-secure AKE protocols.
Supported by the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation programme, grant agreement 802823.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
One can always prove tight \(\mathsf {MU\text {-}} \mathsf {EUF\text {-}CMA} ^{\mathsf {corr}}\) security under the interactive assumption that the scheme is \(\mathsf {MU\text {-}} \mathsf {EUF\text {-}CMA} ^{\mathsf {corr}}\) secure.
- 2.
All known instantiations of lossy identification schemes have a deterministic \(\mathsf {LID}.\mathsf {Prove} _2\) algorithm. However, if a new instantiation requires randomness, then it can be “forwarded” from \(\mathsf {LID}.\mathsf {Prove} _1\) in the state variable \(\mathsf {st}\). Therefore the requirement that \(\mathsf {LID}.\mathsf {Prove} _{2}\) is deterministic is without loss of generality, and only made to simplify our security analysis.
- 3.
This is indeed efficiently possible as
 is a not an e-th residue with probability \(1 - 1/e\) and we can efficiently check whether a given U is an e-th residue when the factorization of N is known [1].
is a not an e-th residue with probability \(1 - 1/e\) and we can efficiently check whether a given U is an e-th residue when the factorization of N is known [1].
References
Abdalla, M., Ben Hamouda, F., Pointcheval, D.: Tighter reductions for forward-secure signature schemes. In: Kurosawa, K., Hanaoka, G. (eds.) PKC 2013. LNCS, vol. 7778, pp. 292–311. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-36362-7_19
Abdalla, M., Fouque, P.-A., Lyubashevsky, V., Tibouchi, M.: Tightly-secure signatures from lossy identification schemes. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 572–590. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_34
Abdalla, M., Fouque, P.-A., Lyubashevsky, V., Tibouchi, M.: Tightly secure signatures from lossy identification schemes. J. Cryptol. 29(3), 597–631 (2016)
Abe, M., Ohkubo, M., Suzuki, K.: 1-out-of-n signatures from a variety of keys. In: Zheng, Y. (ed.) ASIACRYPT 2002. LNCS, vol. 2501, pp. 415–432. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-36178-2_26
Bader, C., Hofheinz, D., Jager, T., Kiltz, E., Li, Y.: Tightly-secure authenticated key exchange. In: Dodis, Y., Nielsen, J.B. (eds.) TCC 2015, Part I. LNCS, vol. 9014, pp. 629–658. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46494-6_26
Bader, C., Jager, T., Li, Y., Schäge, S.: On the impossibility of tight cryptographic reductions. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016, Part II. LNCS, vol. 9666, pp. 273–304. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_10
Bellare, M., Boldyreva, A., Micali, S.: Public-key encryption in a multi-user setting: security proofs and improvements. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 259–274. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45539-6_18
Bellare, M., Rogaway, P.: Entity authentication and key distribution. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 232–249. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48329-2_21
Cachin, C., Micali, S., Stadler, M.: Computationally private information retrieval with polylogarithmic communication. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 402–414. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-48910-X_28
Canetti, R., Krawczyk, H.: Analysis of key-exchange protocols and their use for building secure channels. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 453–474. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44987-6_28
Chaum, D., Evertse, J.-H., van de Graaf, J.: An improved protocol for demonstrating possession of discrete logarithms and some generalizations. In: Chaum, D., Price, W.L. (eds.) EUROCRYPT 1987. LNCS, vol. 304, pp. 127–141. Springer, Heidelberg (1988). https://doi.org/10.1007/3-540-39118-5_13
Cohn-Gordon, K., Cremers, C., Gjøsteen, K., Jacobsen, H., Jager, T.: Highly efficient key exchange protocols with optimal tightness. In: Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019, Part II. LNCS, vol. 11694, pp. 767–797. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26954-8_25
Cramer, R., Damgård, I., Schoenmakers, B.: Proofs of partial knowledge and simplified design of witness hiding protocols. In: Desmedt, Y.G. (ed.) CRYPTO 1994. LNCS, vol. 839, pp. 174–187. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48658-5_19
Davis, H., Günther, F.: Tighter proofs for the sigma and TLS 1.3 key exchange protocols. Cryptology ePrint Archive, Report 2020/1029 (2020). https://eprint.iacr.org/2020/1029
Diemert, D., Jager, T.: On the tight security of TLS 1.3: theoretically-sound cryptographic parameters for real-world deployments. Cryptology ePrint Archive, Report 2020/726; to appear in the Journal of Cryptology (2020). https://eprint.iacr.org/2020/726
Digital Signature Standard (DSS). National Institute of Standards and Technology (NIST), FIPS PUB 186-3, U.S. Department of Commerce (2009). http://csrc.nist.gov/publications/fips/fips186-3/fips_186-3.pdf
Fersch, M., Kiltz, E., Poettering, B.: On the provable security of (EC)DSA signatures. In: Weippl, E.R., Katzenbeisser, S., Kruegel, C., Myers, A.C., Halevi, S (eds.) ACM CCS 2016, pp. 1651–1662. ACM Press, October 2016
Fischlin, M., Harasser, P., Janson, C.: Signatures from sequential-OR proofs. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020, Part III. LNCS, vol. 12107, pp. 212–244. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45727-3_8
Fischlin, M., Lehmann, A., Ristenpart, T., Shrimpton, T., Stam, M., Tessaro, S.: Random oracles with(out) programmability. In: Abe, M. (ed.) ASIACRYPT 2010. LNCS, vol. 6477, pp. 303–320. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-17373-8_18
Fleischhacker, N., Jager, T., Schröder, D.: On tight security proofs for Schnorr signatures. In: Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014, Part I. LNCS, vol. 8873, pp. 512–531. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-45611-8_27
Fleischhacker, N., Jager, T., Schröder, D.: On tight security proofs for Schnorr signatures. J. Cryptol. 32(2), 566–599 (2019)
Garg, S., Bhaskar, R., Lokam, S.V.: Improved bounds on security reductions for discrete log based signatures. In: Wagner, D. (ed.) CRYPTO 2008. LNCS, vol. 5157, pp. 93–107. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85174-5_6
Gjøsteen, K., Jager, T.: Practical and tightly-secure digital signatures and authenticated key exchange. In: Shacham, H., Boldyreva, A. (eds.) CRYPTO 2018, Part II. LNCS, vol. 10992, pp. 95–125. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-96881-0_4
Goldwasser, S., Micali, S., Rivest, R.L.: A digital signature scheme secure against adaptive chosen-message attacks. SIAM J. Comput. 17(2), 281–308 (1988)
Guillou, L.C., Quisquater, J.-J.: A “paradoxical” indentity-based signature scheme resulting from zero-knowledge. In: Goldwasser, S. (ed.) CRYPTO 1988. LNCS, vol. 403, pp. 216–231. Springer, New York (1990). https://doi.org/10.1007/0-387-34799-2_16
Hasegawa, S., Isobe, S.: Lossy identification schemes from decisional RSA. In: International Symposium on Information Theory and its Applications, ISITA 2014, Melbourne, Australia, 26–29 October 2014, pp. 143–147. IEEE (2014)
Hofheinz, D., Jager, T.: Tightly secure signatures and public-key encryption. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 590–607. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_35
Jager, T., Kiltz, E., Riepel, D., Schäge, S.: Tightly-secure authenticated key exchange, revisited. Cryptology ePrint Archive, Report 2020/1279 (2020). https://eprint.iacr.org/2020/1279
Katz, J., Wang, N.: Efficiency improvements for signature schemes with tight security reductions. In: Jajodia, S., Atluri, V., Jaeger, T. (eds.) ACM CCS 2003, pp. 155–164. ACM Press, October 2003
Kiltz, E., Masny, D., Pan, J.: Optimal security proofs for signatures from identification schemes. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016, Part II. LNCS, vol. 9815, pp. 33–61. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53008-5_2
Kiltz, E., O’Neill, A., Smith, A.: Instantiability of RSA-OAEP under chosen-plaintext attack. In: Rabin, T. (ed.) CRYPTO 2010. LNCS, vol. 6223, pp. 295–313. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14623-7_16
Krawczyk, H.: SIGMA: the “SIGn-and-MAc” approach to authenticated Diffie-Hellman and its use in the IKE protocols. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 400–425. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45146-4_24
Li, Y., Schäge, S.: No-match attacks and robust partnering definitions: defining trivial attacks for security protocols is not trivial. In: Thuraisingham, B.M., Evans, D., Malkin, T., Xu, D. (eds.) ACM CCS 2017, pp. 1343–1360. ACM Press, October/November 2017
Liu, X., Liu, S., Gu, D., Weng, J.: Two-pass authenticated key exchange with explicit authentication and tight security. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part II. LNCS, vol. 12492, pp. 785–814. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-64834-3_27
Paillier, P., Vergnaud, D.: Discrete-log-based signatures may not be equivalent to discrete log. In: Roy, B. (ed.) ASIACRYPT 2005. LNCS, vol. 3788, pp. 1–20. Springer, Heidelberg (2005). https://doi.org/10.1007/11593447_1
Schnorr, C.P.: Efficient identification and signatures for smart cards. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 239–252. Springer, New York (1990). https://doi.org/10.1007/0-387-34805-0_22
Seurin, Y.: On the exact security of Schnorr-type signatures in the random oracle model. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 554–571. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_33
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Proof of Theorem 20
Random Self-reducibility of DDH. It is well-known that the DDH problem is random self-reducible, which we summarize in the following lemma. See [7, Lemma 5.2] for a proof.
Lemma 22
There exists an efficient algorithm \(\mathsf {ReRand} \) that takes as input (g, h) and a DDH instance \((u,v) \in \mathbb {G} ^{2}\) and an integer \(N \), and outputs \(N \) new DDH instances \((u^{(i)},v^{(i)})\) such that
for all \(i \in [N ]\). The running time of this algorithm mainly consists of \(\mathcal O(N)\) exponentiations in \(\mathbb {G} \).
Proof. To show that \(\mathsf {LID} \) is lossy, we need to show that it satisfies all properties presented in Definition 4.
-
Completeness of normal keys. We claim that the above scheme is perfectly-complete. To prove this, we show that for any honest transcript it holds that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\). Let
 be an (honest) key pair and let \((\mathsf {cmt}, \mathsf {ch}, \mathsf {resp})\) be an honest transcript, that is,
be an (honest) key pair and let \((\mathsf {cmt}, \mathsf {ch}, \mathsf {resp})\) be an honest transcript, that is,  ,
,  and
and 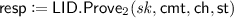 . By definition of the scheme, we have \( pk = (g,h,u,v)\) with \((u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \) and \( sk = x\) and \(\mathsf {cmt} = (e,f) = (g^r, h^r)\) and \(\mathsf {resp} = r - \mathsf {ch} \cdot x\). Further, \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\) if and only if \(e = g^\mathsf {resp} \cdot u^\mathsf {ch} \) and \(f = h^\mathsf {resp} \cdot v^\mathsf {ch} \). Observe that $$ g^\mathsf {resp} \cdot u^\mathsf {ch} = g^{r - \mathsf {ch} \cdot x} \cdot g^{\mathsf {ch} \cdot x} = g^r = e. $$
. By definition of the scheme, we have \( pk = (g,h,u,v)\) with \((u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \) and \( sk = x\) and \(\mathsf {cmt} = (e,f) = (g^r, h^r)\) and \(\mathsf {resp} = r - \mathsf {ch} \cdot x\). Further, \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\) if and only if \(e = g^\mathsf {resp} \cdot u^\mathsf {ch} \) and \(f = h^\mathsf {resp} \cdot v^\mathsf {ch} \). Observe that $$ g^\mathsf {resp} \cdot u^\mathsf {ch} = g^{r - \mathsf {ch} \cdot x} \cdot g^{\mathsf {ch} \cdot x} = g^r = e. $$An analogous equation holds for f if g is replaced by h. Hence, \(\mathsf {LID}.\mathsf {Vrfy} \) outputs 1 for every honest transcript.
-
Simulatability of transcripts. We claim that the above scheme is perfectly simulatable. To show this, we need to argue that the two distributions

and

are identical. Recall that we have \( pk = (g,h,u,v)\) with \((u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \), \( sk = x\), \(\mathsf {cmt} = (e,f) = (g^r, h^r)\) with
 , and \(\mathsf {resp} = r - \mathsf {ch} \cdot x\) for an honest transcript (i.e., in the former distribution). Thus, we have that \(\mathsf {cmt} = (e,f)\) is uniformly distributed over \(\mathbb {G} ^2\). Consequently, since
, and \(\mathsf {resp} = r - \mathsf {ch} \cdot x\) for an honest transcript (i.e., in the former distribution). Thus, we have that \(\mathsf {cmt} = (e,f)\) is uniformly distributed over \(\mathbb {G} ^2\). Consequently, since  and
and  , we also have that the response \(\mathsf {resp} \) is distributed uniformly and independently (of \(\mathsf {cmt} \) and \(\mathsf {ch} \)) over \(\mathbb {Z} _q\).
, we also have that the response \(\mathsf {resp} \) is distributed uniformly and independently (of \(\mathsf {cmt} \) and \(\mathsf {ch} \)) over \(\mathbb {Z} _q\).We will now take a look at the later distribution. Note that \(\mathsf {ch}\) and \(\mathsf {resp}\) are both uniformly random elements over \(\mathbb {Z} _p\). It remains to show that \(\mathsf {cmt} \) in the simulated transcript is distributed uniformly over \(\mathbb {G} ^2\).
Recall that
 is defined as
is defined as  . Observe that \(\log _g(e) = \mathsf {resp} + \mathsf {ch} \cdot x\) and \(\log _g(f) = \log _g(h) \cdot \left( \mathsf {resp} + \mathsf {ch} \cdot x \right) \). Since
. Observe that \(\log _g(e) = \mathsf {resp} + \mathsf {ch} \cdot x\) and \(\log _g(f) = \log _g(h) \cdot \left( \mathsf {resp} + \mathsf {ch} \cdot x \right) \). Since  and
and  , we have that both \(\log _g(e)\) and \(\log _g(f)\) are distributed uniformly and independently (of \(\mathsf {ch} \) and \(\mathsf {resp} \)) over \(\mathbb {Z} _q\) and thus (e, f) is distributed uniformly over \(\mathbb {G} ^2\). Note that e, f are not distributed independently of each other (as it is the case in the honest transcript).
, we have that both \(\log _g(e)\) and \(\log _g(f)\) are distributed uniformly and independently (of \(\mathsf {ch} \) and \(\mathsf {resp} \)) over \(\mathbb {Z} _q\) and thus (e, f) is distributed uniformly over \(\mathbb {G} ^2\). Note that e, f are not distributed independently of each other (as it is the case in the honest transcript). -
Indistinguishability of keys. As already remarked above, honest keys contain a DDH tuple, whereas lossy keys contain a non-DDH tuple. Therefore, we claim that for every adversary \(\mathcal {A} \) trying to distinguish honest from lossy keys of \(\mathsf {LID} \), we can construct an adversary \(\mathcal {B} \) such that

To prove this claim, we give a construction of \(\mathcal {B} \) running \(\mathcal {A} \) as a subroutine. The adversary \(\mathcal {B} \) receives a tuple (g, h, u, v) such that (u, v) either is a DDH tuple (i.e., \((u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \)) or not. Then, it uses the algorithm of Lemma 22 to re-randomize (u, v) into N tuples
 such that $$ (u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \iff \forall i \in [N] : (u^{(i)}, v^{(i)}) \in \mathsf {DDH}(\mathbb {G}, g, h) $$
such that $$ (u,v) \in \mathsf {DDH}(\mathbb {G}, g, h) \iff \forall i \in [N] : (u^{(i)}, v^{(i)}) \in \mathsf {DDH}(\mathbb {G}, g, h) $$and hands \(( pk _i = (g,h,u^{(i)}, v^{(i)}))_{i \in [N]}\) to \(\mathcal {A} \) as input. When \(\mathcal {A} \) halts and outputs a bit b, \(\mathcal {B} \) halts and outputs b as well. Observe that by Lemma 22, we have
$$ \Pr [ \mathcal {B} (g,h,u,v) = 1 ] \ge \Pr [ \mathcal {A} ( pk ^{(1)}, \dotsc , pk ^{(N)}) ] $$with
 ,
,  , and
, and  . Further, we have $$ \Pr [ \mathcal {B} (g,h,\bar{u},\bar{v}) = 1 ] \ge \Pr [ \mathcal {A} ( pk '^{(1)}, \dotsc , pk '^{(N)}) ] $$
. Further, we have $$ \Pr [ \mathcal {B} (g,h,\bar{u},\bar{v}) = 1 ] \ge \Pr [ \mathcal {A} ( pk '^{(1)}, \dotsc , pk '^{(N)}) ] $$with
 ,
,  for every \(i \in [N]\), and
for every \(i \in [N]\), and  . In conclusion, we have
. In conclusion, we have 
-
Lossiness. We claim that the above scheme \(\mathsf {LID} \) is 1/q-lossy. To show this, we first recall a classical result showing the soundness of the protocol to “prove DDH tuples” by Chaum et al. presented above. Namely, we claim that if \(\log _g(u) \ne \log _h(v)\) holds for the public key \( pk = (g,h,u,v)\) (i.e., \( pk \) is a lossy key and \((u,v) \not \in \mathsf {DDH}(\mathbb {G}, g, h) \)), for any commitment \(\mathsf {cmt} \) there can only be at most one challenge \(\mathsf {ch} \) such that the transcript is valid. We prove this statement by contradiction.
Let \(\mathcal {A} \) be an unbounded adversary that on input of a lossy public key
 , outputs commitment \(\mathsf {cmt} = (e,f)\). We now show that \(\mathcal {A} \) can only output a correct \(\mathsf {resp} \) for one \(\mathsf {ch} \) such that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\). Suppose that \(\mathcal {A} \) was able to come up with two responses \(\mathsf {resp} _1\) and \(\mathsf {resp} _2\) for two different challenge \(\mathsf {ch} _1 \ne \mathsf {ch} _2\) such that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch} _1, \mathsf {resp} _1) = 1\) and \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch} _2, \mathsf {resp} _2) = 1\) holds. This implies by the definition of \(\mathsf {LID}.\mathsf {Vrfy} \) that $$ e = g^{\mathsf {resp} _1} u^{\mathsf {ch} _1} = g^{\mathsf {resp} _2} u^{\mathsf {ch} _2} \qquad \text{ and } \qquad f = h^{\mathsf {resp} _1} v^{\mathsf {ch} _1} = h^{\mathsf {resp} _2} v^{\mathsf {ch} _2}. $$
, outputs commitment \(\mathsf {cmt} = (e,f)\). We now show that \(\mathcal {A} \) can only output a correct \(\mathsf {resp} \) for one \(\mathsf {ch} \) such that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\). Suppose that \(\mathcal {A} \) was able to come up with two responses \(\mathsf {resp} _1\) and \(\mathsf {resp} _2\) for two different challenge \(\mathsf {ch} _1 \ne \mathsf {ch} _2\) such that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch} _1, \mathsf {resp} _1) = 1\) and \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch} _2, \mathsf {resp} _2) = 1\) holds. This implies by the definition of \(\mathsf {LID}.\mathsf {Vrfy} \) that $$ e = g^{\mathsf {resp} _1} u^{\mathsf {ch} _1} = g^{\mathsf {resp} _2} u^{\mathsf {ch} _2} \qquad \text{ and } \qquad f = h^{\mathsf {resp} _1} v^{\mathsf {ch} _1} = h^{\mathsf {resp} _2} v^{\mathsf {ch} _2}. $$Equivalently, we get by using the assumption that \(\mathsf {ch} _1 \ne \mathsf {ch} _2\):
$$ \log _g(u) = \frac{(\mathsf {resp} _1 - \mathsf {resp} _2)}{\mathsf {ch} _2 - \mathsf {ch} _1} \qquad \text{ and } \qquad \log _h(v) = \frac{(\mathsf {resp} _1 - \mathsf {resp} _2)}{\mathsf {ch} _2 - \mathsf {ch} _1}. $$However, this is a contraction to the assumption that \(\log _g(u) \ne \log _h(v)\). Thus, \( pk \) must be a lossy key.
Using this, we have that for every commitment \(\mathcal {A} \) outputs, there can only be at most one challenge \(\mathsf {ch} \) such that the adversary generated a valid transcript. Note that we have an unbounded adversary and based on \(\mathsf {cmt} \) and \(\mathsf {ch} \) it can compute a response. As there is only one challenge for \(\mathsf {cmt} \) output by \(\mathcal {A} \) and the challenge is chosen uniformly at random, the adversary can only win with a probability of at most 1/q.
-
Uniqueness with respect to lossy keys. Let \( pk = (g,h,u,v)\) with \((u,v) \not \in \mathsf {DDH}(\mathbb {G}, g, h) \) and \((\mathsf {cmt}, \mathsf {ch}, \mathsf {resp})\) with \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp}) = 1\). Suppose that there is a \(\mathsf {resp} ' \ne \mathsf {resp} \) such that \(\mathsf {LID}.\mathsf {Vrfy} ( pk , \mathsf {cmt}, \mathsf {ch}, \mathsf {resp} ') = 1\). In this case, we have for \(\mathsf {cmt} = (e,f)\) that
$$ e = g^\mathsf {resp} u^\mathsf {ch} = g^{\mathsf {resp} '} u^\mathsf {ch} \qquad \text{ and } \qquad f = h^\mathsf {resp} v^\mathsf {ch} = h^{\mathsf {resp} '} v^\mathsf {ch}. $$However, this implies that
$$ g^\mathsf {resp} = g^{\mathsf {resp} '} \qquad \text{ and } \qquad h^\mathsf {resp} = h^{\mathsf {resp} '}, $$which implies that \(\mathsf {resp} = \mathsf {resp} '\), contradicting the initial assumption.
-
Min-entropy. For any secret key \( sk \), the commitment
 equals \((g^r,h^r)\) for
equals \((g^r,h^r)\) for  , which is independent of \( sk \). So the min-entropy of \(\mathsf {cmt} \) is \(\alpha =\log _2(q)\).
, which is independent of \( sk \). So the min-entropy of \(\mathsf {cmt} \) is \(\alpha =\log _2(q)\). -
Commitment-recoverable. The verification algorithm of \(\mathsf {LID} \) first recovers a commitment using the simulator and then compares the result with the commitment in the transcript. So \(\mathsf {LID}\) is commitment-recoverable.
-
Injective simulator. For any normal public key \( pk =(g,h,u,v)\), any response \(\mathsf {resp}\) and any challenge \(\mathsf {ch} \ne \mathsf {ch} '\), we have that
$$\begin{aligned} \begin{aligned} \mathsf {LID}.\mathsf {Sim} ( pk , \mathsf {ch}, \mathsf {resp})&= (g^{\mathsf {resp}} u^{\mathsf {ch}}, h^{\mathsf {resp}} v^{\mathsf {ch}}),\\ \mathsf {LID}.\mathsf {Sim} ( pk , \mathsf {ch} ', \mathsf {resp})&= (g^{\mathsf {resp}} u^{\mathsf {ch} '}, h^{\mathsf {resp}} v^{\mathsf {ch} '}). \end{aligned} \end{aligned}$$Thus, if the above two pairs are equal, we must have that \((u^{\mathsf {ch}}, v^{\mathsf {ch}}) = (u^{\mathsf {ch} '}, v^{\mathsf {ch} '})\). That implies \(\mathsf {ch} = \mathsf {ch} '\).
\(\square \)
B Proof of Theorem 21
The following definition is from [1].
Definition 23
(RSA modulus generation algorithm). Let \(\ell _N\) be a positive integer and let \(\mathsf {RSA}_{\ell _N}\) be the set of all tuples \((N,p_1,p_2)\) such that \(N=p_1p_2\) is a \(\ell _N\)-bit number and \(p_1,p_2\) are two distinct primes in the set of \(\ell _N/2\)-bit primes \(\mathbb {P}_{\ell _N/2}\). Let R be any relation on \(p_1\) and \(p_2\), define \(\mathsf {RSA}_{\ell _N}[R]:=\{(N,p_1,p_2)\in \mathsf {RSA}_{\ell _N} \mid R(p_1,p_2)=1\}\).
We can use it to define the n-fold higher residuosity assumption as well as the \(\phi \)-hiding assumption [1, 9, 31].
Definition 24
(n-fold higher residuosity assumption). Let e be a random prime of length \(\ell _e\le \ell _N/4\) and

and let \(\mathsf {HR}_{N}[e]:=\{g^e\bmod N \mid g\in \mathbb {Z} _N^*\}\) be the set of e-th residues modulo N. We define the advantage of any \(\mathcal {A}\) in solving the higher residuosity problem as
where  and
and  . The e-residuosity problem is \((t,\varepsilon )\)-hard if for any \(\mathcal {A}\) with running time at most t, \(\mathsf {Adv}_{}^{n\text {-}\mathsf {HR}} (\mathcal {A})\) is at most \(\varepsilon \).
. The e-residuosity problem is \((t,\varepsilon )\)-hard if for any \(\mathcal {A}\) with running time at most t, \(\mathsf {Adv}_{}^{n\text {-}\mathsf {HR}} (\mathcal {A})\) is at most \(\varepsilon \).
We prove the following lemma.
Lemma 25
For any adversary \(\mathcal {A}\) with running time \(t_\mathcal {A} \) against the n-key-indistinguishability of \(\mathsf {LID}\) in Fig. 2, we can construct an adversary \(\mathcal {B} \) with running time \(t_{\mathcal {B}}\approx t_\mathcal {A} \) such that

Proof
The proof is a straightforward reduction. \(\mathcal {B} \) receives \((N,e,y_{1}, \ldots , y_{n})\) as input and defines the common parameters as (N, e) and
Note that this defines real keys if the \(y_{i}\) are e-th residues, and lossy keys if the \(y_{i}\) are e-th non-residues. \(\square \)
Finally, we can show that the n-fold higher residuosity assumption is tightly implied by the \(\phi \)-hiding assumption, for any polynomially-bounded n.
Definition 26
(\(\phi \)-hiding assumption [1, 9, 31]). Let \(c\le 1/4\) be a constant. For any adversary \(\mathcal {A}\), define the advantage of \(\mathcal {A}\) in solving the \(\phi \)-hiding problem to be
where  ,
,  and
and  . The \(\phi \)-hiding problem is \((t,\varepsilon )\)-hard if for any \(\mathcal {A}\) with running time at most t, \(\mathsf {Adv}_{}^{\phi \text {H}} (\mathcal {A})\) is at most \(\varepsilon \).
. The \(\phi \)-hiding problem is \((t,\varepsilon )\)-hard if for any \(\mathcal {A}\) with running time at most t, \(\mathsf {Adv}_{}^{\phi \text {H}} (\mathcal {A})\) is at most \(\varepsilon \).
Lemma 27
For any adversary \(\mathcal {A}\) with running time \(t_\mathcal {A} \) we can construct an adversary \(\mathcal {B} \) with running time \(t_{\mathcal {B}}\approx t_\mathcal {A} \) such that
Proof
First, we have that
where  and
and  . We can prove the following claim.
. We can prove the following claim.
Claim
\(\left| \Pr [\mathcal {A} (N,e,y_{1}, \ldots , y_{n})=1] - \Pr [\mathcal {A} (N',e,y'_{1}, \ldots , y'_{n})=1] \right| \le \mathsf {Adv}_{}^{\phi \text {H}} (\mathcal {B})\).
The proof is again a very straightforward reduction. \(\mathcal {B} \) receives as input (N, e). It samples  uniformly random and then defines \(y_{i} := x_{i}^{e} \bmod N\) for \(i \in \{1, \ldots , n\}\). Then it runs \(\mathcal {A} \) on input \((N,e,y_{1}, \ldots , y_{n})\) and returns whatever \(\mathcal {A} \) returns.
uniformly random and then defines \(y_{i} := x_{i}^{e} \bmod N\) for \(i \in \{1, \ldots , n\}\). Then it runs \(\mathcal {A} \) on input \((N,e,y_{1}, \ldots , y_{n})\) and returns whatever \(\mathcal {A} \) returns.
Note that if (N, e) is a “lossy” key, so that \(e \mid \phi (N)\), then the \(y_{i}\) are random e-th residues. However, if \(\gcd (e, \phi (N))=1\), then all \(y_{i}\) are random e-th non-residues, since the map \(x \mapsto x^{e} \bmod N\) is a permutation.
Using a similar idea, we can prove that
Claim
\(\left| \Pr [\mathcal {A} (N',e,y'_{1}, \ldots , y'_{n})=1] - \Pr [\mathcal {A} (N,e,y'_{1}, \ldots , y'_{n})=1] \right| \le \mathsf {Adv}_{}^{\phi \text {H}} (\mathcal {B})\).
Putting the two claims together, we have that \(\mathsf {Adv}_{}^{n\text {-}\mathsf {HR}} (\mathcal {A}) \le 2\mathsf {Adv}_{}^{\phi \text {H}} (\mathcal {B})\) and Lemma 27 follows. \(\square \)
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Diemert, D., Gellert, K., Jager, T., Lyu, L. (2021). More Efficient Digital Signatures with Tight Multi-user Security. In: Garay, J.A. (eds) Public-Key Cryptography – PKC 2021. PKC 2021. Lecture Notes in Computer Science(), vol 12711. Springer, Cham. https://doi.org/10.1007/978-3-030-75248-4_1
Download citation
DOI: https://doi.org/10.1007/978-3-030-75248-4_1
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-75247-7
Online ISBN: 978-3-030-75248-4
eBook Packages: Computer ScienceComputer Science (R0)


 is a not an e-th residue with probability
is a not an e-th residue with probability  be an (honest) key pair and let
be an (honest) key pair and let  ,
,  and
and 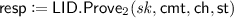 . By definition of the scheme, we have
. By definition of the scheme, we have 

 , and
, and  and
and  , we also have that the response
, we also have that the response  is defined as
is defined as  . Observe that
. Observe that  and
and  , we have that both
, we have that both 
 such that
such that  ,
,  , and
, and  . Further, we have
. Further, we have  ,
,  for every
for every  . In conclusion, we have
. In conclusion, we have 
 , outputs commitment
, outputs commitment  equals
equals  , which is independent of
, which is independent of 